ConfigMgr Current Branch version 1710 now has a hotfix (KB4057517) available which addresses some issues, which you can read up here. The following are the fixes resolved with this hotfix (there are 13 of them):
- Clients who use Azure Active Directory (Azure AD) for authentication do not successfully communicate with a management point
- The Configuration Manager console may terminate unexpectedly after you browse to a content location in the Office 365 Client Installation wizard
- Download of express updates may fail on Windows 10 clients because of an issue that affects files in temporary and cache folders
- Configuration Manager current branch, version 1710 clients are not upgraded on systems that are running Windows Server 2008 SP2. The client Setup program, Ccmsetup.exe, terminates unexpectedly
- The Office 365 Application Installation Wizard may try to download content from an incorrect channel. This causes download failures
- The fallback time that is configured for content is not honored if distribution points or their content are inaccessible
- The Client Notification Restart request is processed incorrectly by remote management points. This causes a .bld notification file to be left in the \MP\Outboxes\bgb.box folder on the remote management point
- Retrying a large single-file download, such as an Office 365 update file, may fail on a site server
- The Persist content in the client cache setting on Package Properties is not honored by clients
- Decommission-related State messages from co-managed client computers are processed incorrectly
- State messages sent by Azure AD users may not be processed
- If a Configuration Manager client restarts during the process of retrying a task sequence policy download, that task sequence does not run automatically after the restart
- Conditional access policies may block access to Office 365 applications for domain-joined devices after migrating to Intune standalone
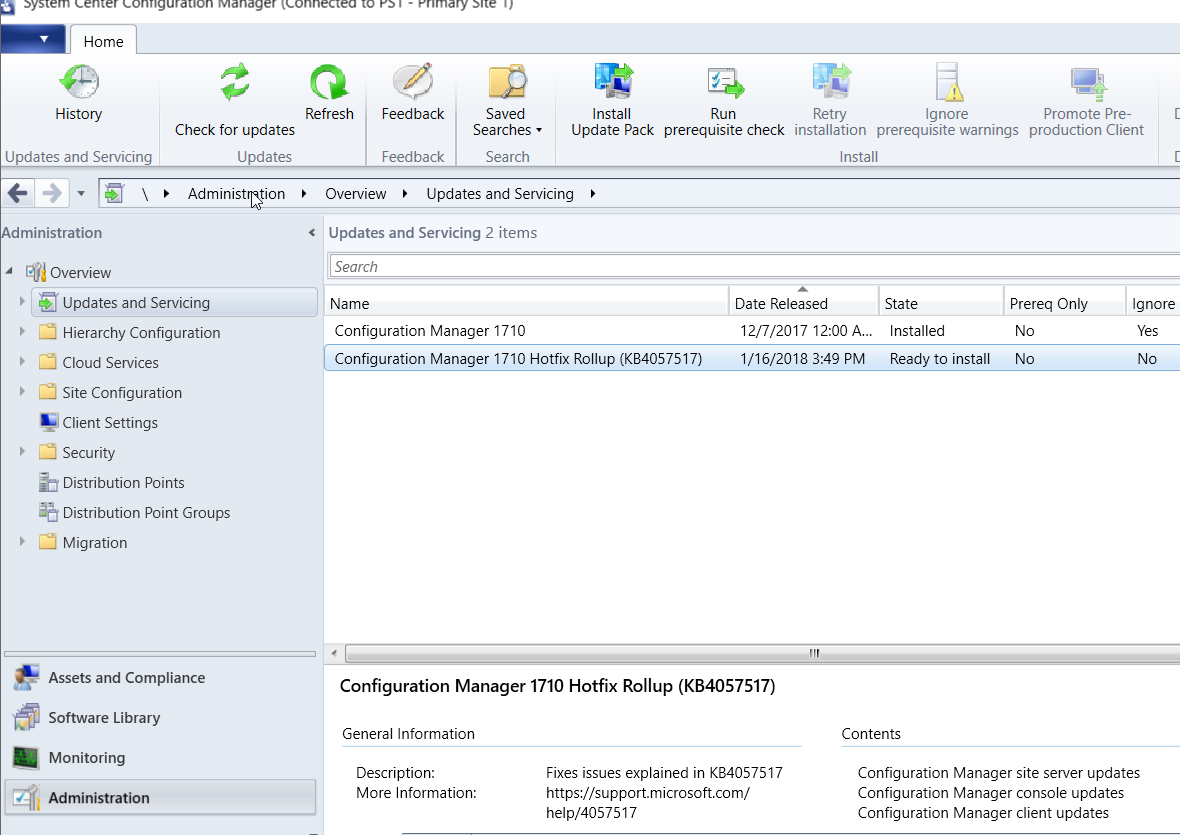
Here are the steps on how to install this hotfix. You will find it available in the ConfigMgr console under Administration > Updates and Servicing. If you don’t see it, click on Check for Updates in the menu ribbon.
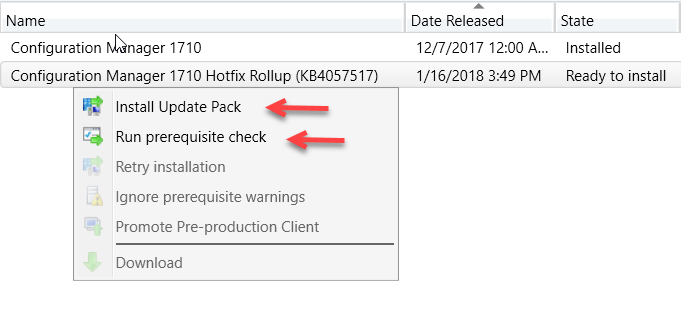
Right-click on Configuration Manager 1710 Hotfix Rollup (KB4057517) and click on Install Update Pack. I recommend that you run the prerequisite check first to make sure there are not issues reported with your site server.
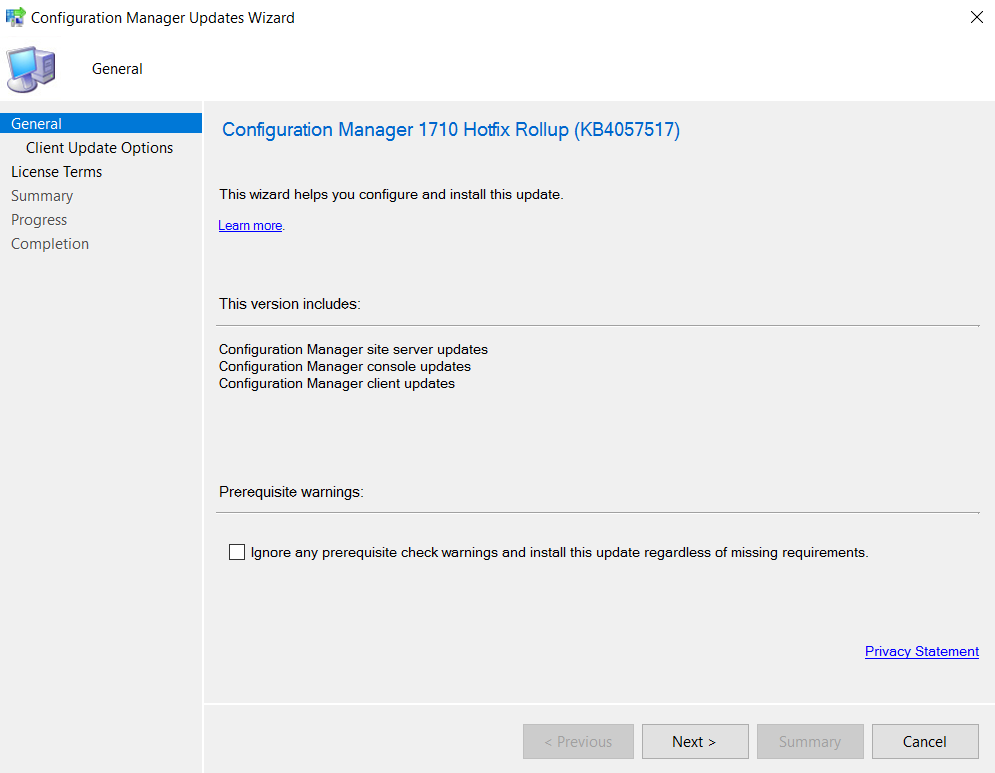
Click Next and select the checkbox if you want to ignore the prerequisite check warning.
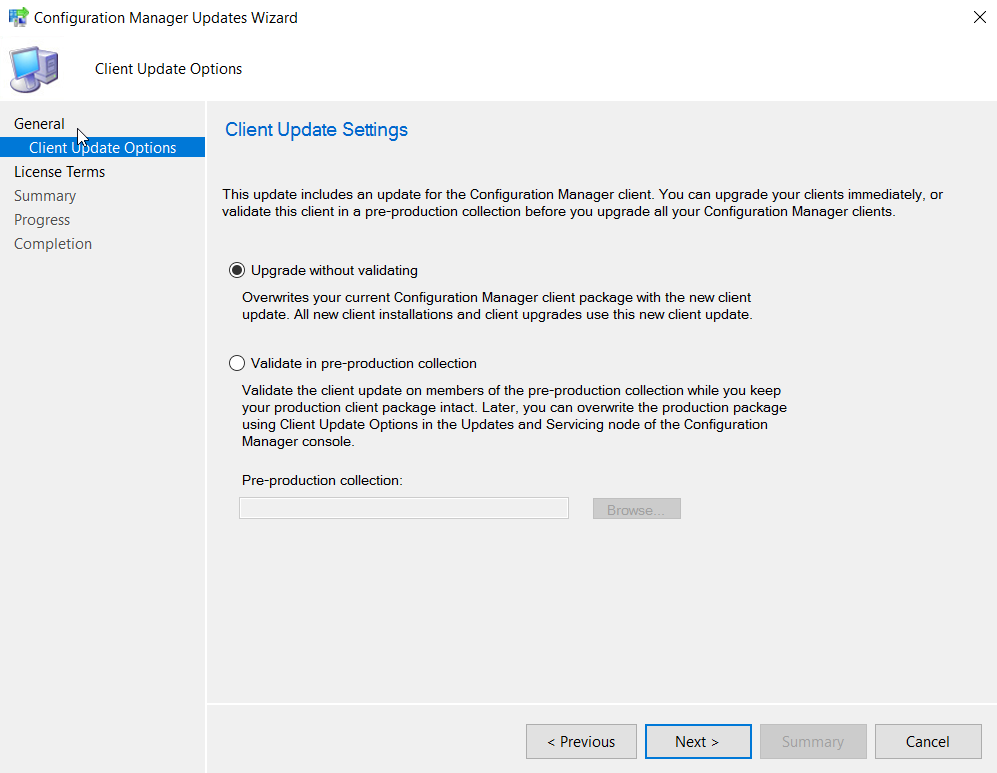
Pick your option to validate or not to validate the upgrade against a collection. I generally tend to select Validate in pre-production collection and choose one of my test collections for the first phase of the upgrade.
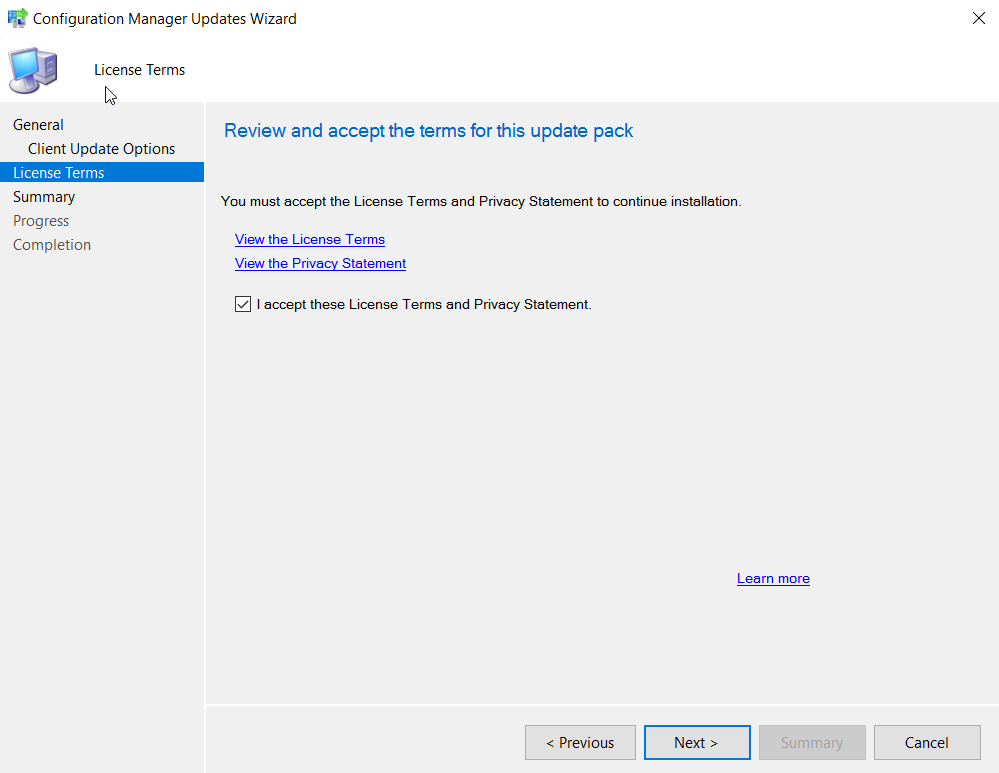
Select the license terms and click Next.
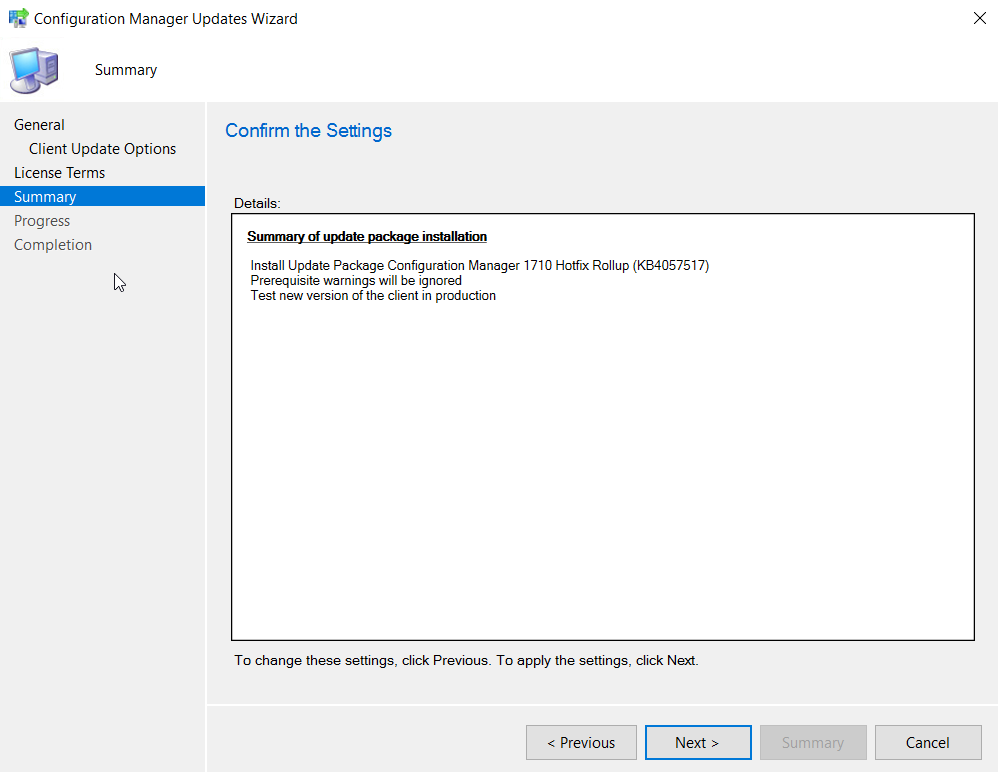
Click Next to confirm the settings.
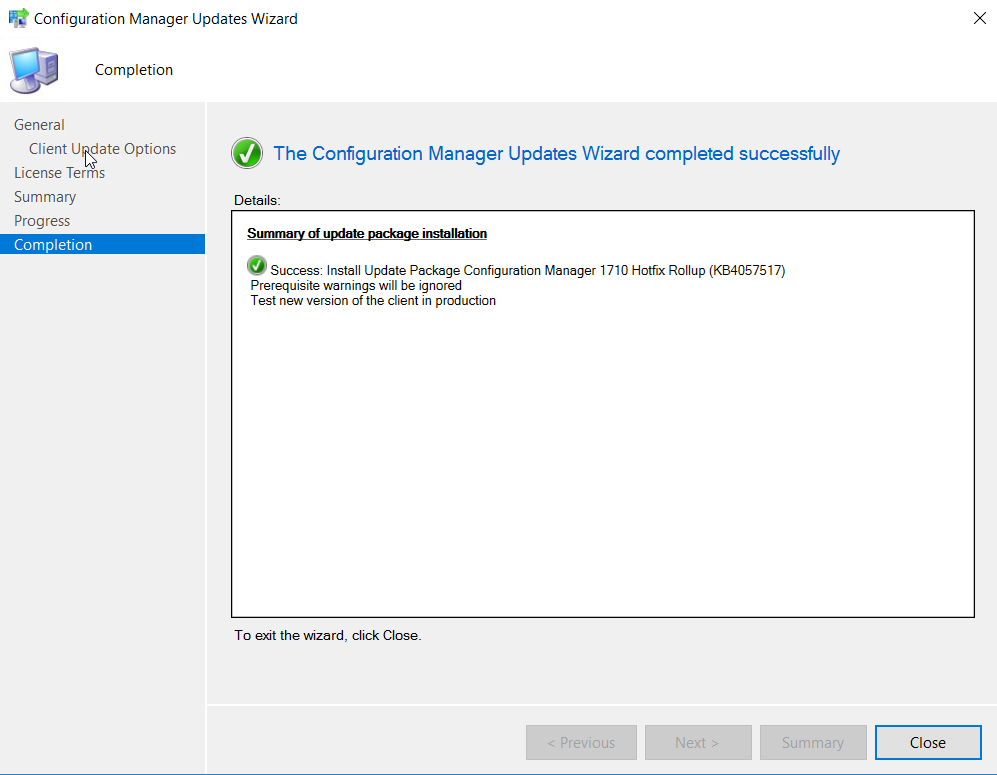
Click Close.
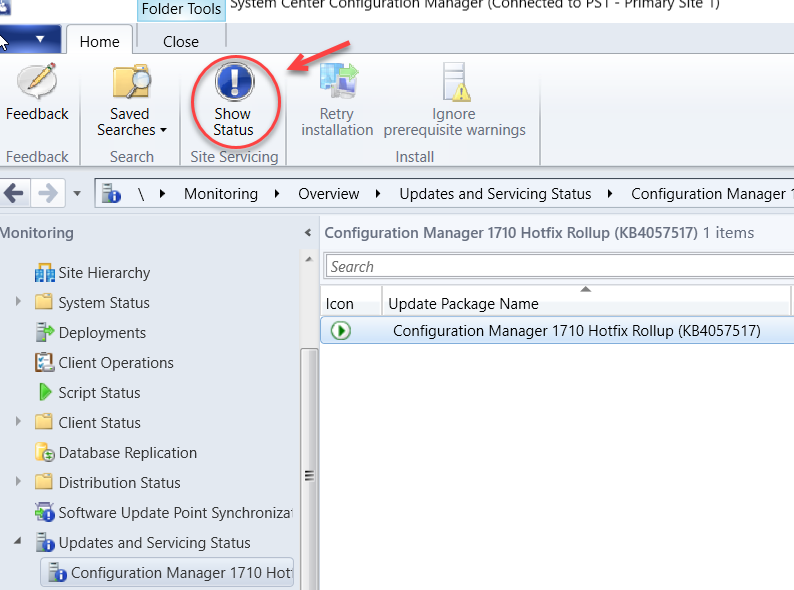
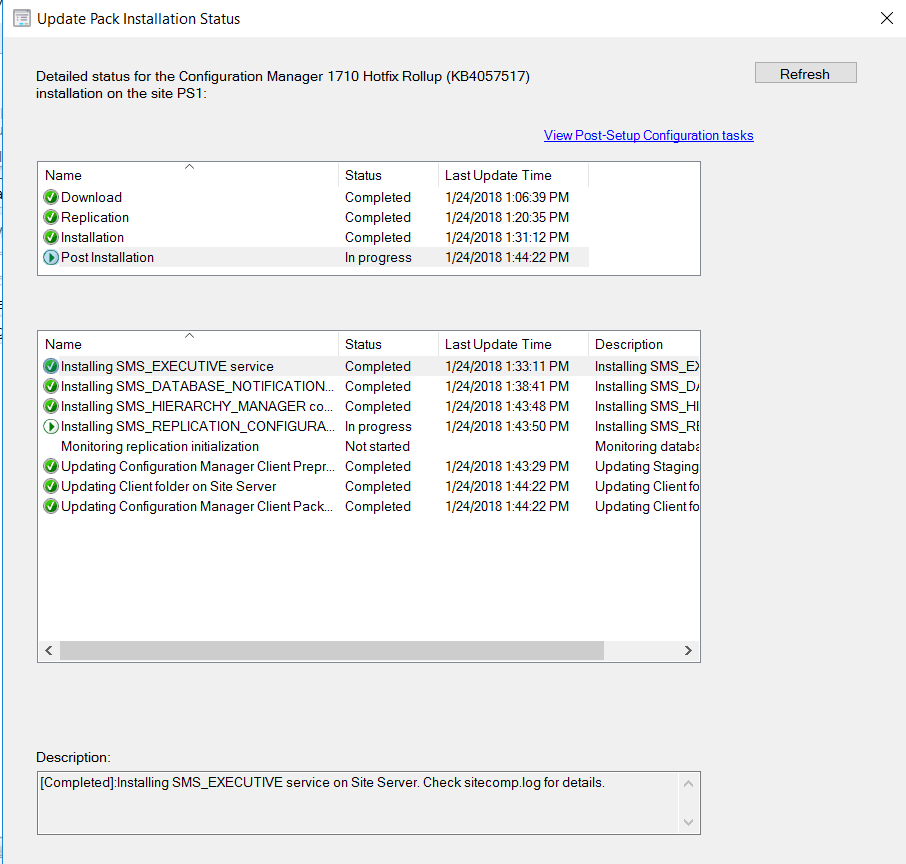
You can now monitor the status of the upgrade under Monitoring > Updates and Servicing Status. Then select the update package name and click on Show Status in the menu ribbon.
The window below will show the stages of the upgrade process where you can monitor it’s progress. If there are any issues, you will see it listed here with a warning and the details provided in the description box in the bottom of the window.
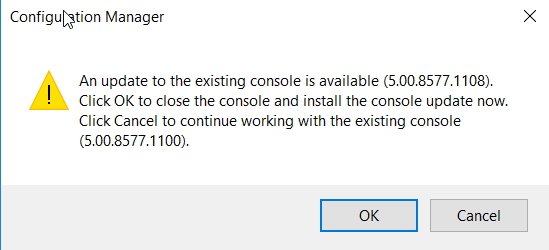
Upon successful completion of the hotfix installation, you will be presented with the pop-up window as seen below to indicate a console upgrade from version 5.0.0.8577.1100 to 5.0.0.8577.1108 is available.
You can verify the console upgrade in the About System Center Configuration Manager drop down menu from the console.
Version 1710
Console version: 5.0.0.8577.1108
Site version: 5.0.8577.1000
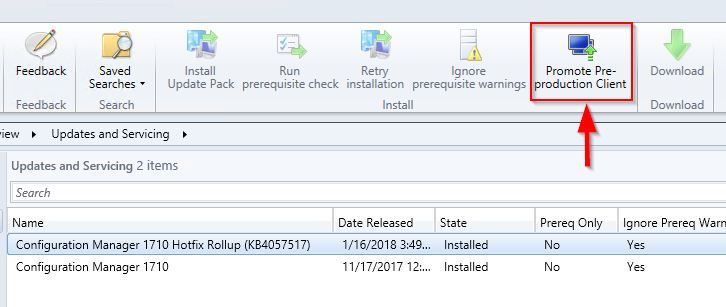
Once you are comfortable with the client upgrade on your test collection which you selected during the validate in pre-production collection phase, you can deploy the client upgrade to all clients in the hierarchy by selecting the Promote Pre-production Client option as seen below.
Your ConfigMgr site is now upgraded with the KB4057517 hotfix.