
Microsoft has released fixes for 56 vulnerabilities, with 11 updates classified as Critical and 43 as Important. Here’s an updated announcement (2021-02-09) from Microsoft: Deploy Windows SSUs and LCUs together with one cumulative update –
Beginning with the February 2021 LCU, we will now publish all future cumulative updates and SSUs for Windows 10, version 2004 and above together as one cumulative monthly update to the normal release category in WSUS.
LCU = Latest Cummulative Update
SSU – Servicing Stack Update
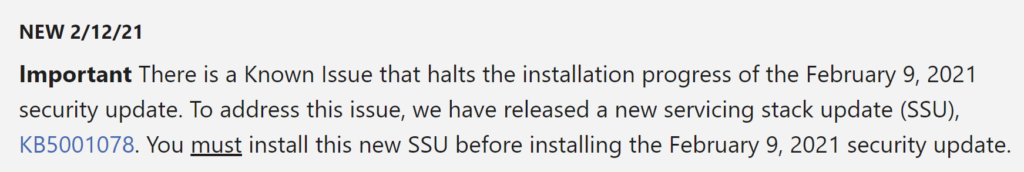
UPDATE – 2021-02-21
KB4301818 > KB5001078
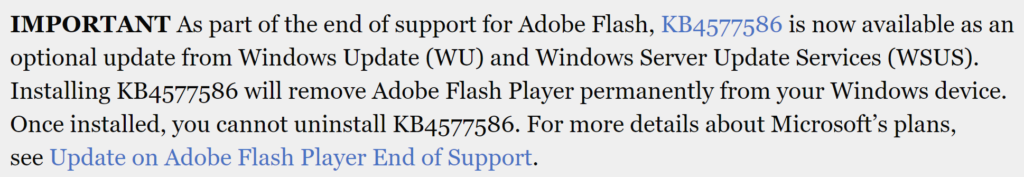
UPDATE – 2021-02-17
KB4577586
Windows 10 Updates for February 2021:
- KB4601319 (OS Builds 19041.804 and 19042.804) for Windows 10 version 20H2 / 2004
- KB4601315 (OS Build 18363.1377) for Windows 10, version 1909
- KB5001028 (OS Build 18363.1379) Out-of-band for Windows 10, version 1909
- KB4601345 (OS Build 17763.1757) for Windows 10 version 1809
- KB4601354 (OS Build 17134.2026) for Windows 10 version 1803
- KB4601330 (OS Build 15063.2642) for Windows 10 version 1703
- KB4601318 (OS Build 14393.4225) for Windows 10 version 1607
- KB4601331 (OS Build 10240.18842) for Windows 10, initial release
Additional February 2021 Patching Resources:
- MSRC – February 2021 Security Updates
- Security Update Guide – Microsoft Security Vulnerabilities
- Internet Explorer 11 zero-day vulnerability gets unofficial micro-patch
- Windows 10 v1909 receives KB5001028 out-of-band fix for WPA3 Wi-Fi
- Advisory ADV990001 for the latest service stack update (SSU)
- Intel fixes vulnerabilities in Windows, Linux graphics drivers
- Adobe Security patches
- Cisco Security patches
- Apple Security patches
- Android Security Bulletin
- Oracle Security Alerts
- Scan Changes and certificates add security for Windows devices using WSUS for updates
- Netlogon Domain Controller Enforcement Mode enabled by default on February 9, 2021
- Zero Day Initiative blog
- SAP February 2021 Security Updates
- Google fixes severe Golang Windows RCE vulnerability
- Apple fixes SUDO root privilege escalation flaw in macOS
Patched publicly disclosed vulnerabilities:
- CVE-2021-1721 – .NET Core and Visual Studio Denial of Service Vulnerability
- CVE-2021-1727 – Windows Installer Elevation of Privilege Vulnerability
- CVE-2021-1733 – Sysinternals PsExec Elevation of Privilege Vulnerability
- CVE-2021-24098 – Windows Console Driver Denial of Service Vulnerability
- CVE-2021-24106 – Windows DirectX Information Disclosure Vulnerability
- CVE-2021-26701 – .NET Core Remote Code Execution Vulnerability
Intel microcode updates for Windows:
Microsoft has also released Intel microcode updates for Windows 10 20H2, 2004, 1909, and older versions to fix issues impacting current and previously released Windows 10 versions.
These microcode updates are offered to affected devices via Windows Update but they can also be manually downloaded directly from the Microsoft Catalog using these links:
- KB4589212: Intel microcode updates for Windows 10, version 2004 and 20H2, and Windows Server, version 2004 and 20H2
- KB4589211: Intel microcode updates for Windows 10, version 1903 and 1909, and Windows Server, version 1903 and 1909
- KB4589208: Intel microcode updates for Windows 10, version 1809 and Windows Server 2019
- KB4589206: Intel microcode updates for Windows 10, version 1803
- KB4589210: Intel microcode updates for Windows 10, version 1607 and Windows Server 2016
- KB4589198: Intel microcode updates for Windows 10, version 1507
On February 9, 2021, Microsoft released security updates affecting the following Microsoft products:
| Product Family | Maximum Severity | Maximum Impact | Associated KB Articles and/or Support Webpages |
| Windows 10 v20H2, v2004, v1909, v1809, and v1803 | Critical | Remote Code Execution | Windows 10 v2004 and Windows 10 v20H2: 4601319 Windows 10 v1909: 4601315 Windows 10 v1809: 4601345 Windows 10 v1803: 4601354 |
| Windows Server 2019, Windows Server 2016, and Server Core installations (2019, 2016, v20H2, v2004, and v1909) | Critical | Remote Code Execution | Windows Server 2019: 4601345 Windows Server 2016: 4601318 Windows Server v2004 and Windows Server v20H2: 4601319 Windows Server v1909: 4601315 |
| Windows 8.1, Windows Server 2012 R2, and Windows Server 2012 | Critical | Remote Code Execution | Windows 8.1 and Windows Server 2012 R2 Monthly Rollup: 4601384 Windows 8.1 and Windows Server 2012 R2 Security Only: 4601349 Windows Server 2012 Monthly Rollup: 4601348 Windows Server 2012 Security Only: 4601357 |
| Microsoft Office-related software | Important | Remote Code Execution | 4493211, 4493222, 4493196, 4493192, 4493204 |
| Microsoft SharePoint-related software | Important | Remote Code Execution | 4493210, 4493194, 4493195, 4493223 |
| Microsoft Lync/Skype for Business | Important | Denial of Service | 5000675, 5000688 |
| Microsoft Exchange Server | Important | Spoofing | 4602269, 4571787 |
| Microsoft .NET-related software | Critical | Remote Code Execution | 4601318, 4601050, 4601887, 4603004, 4602960, 4603005, 4602961, 4601354, 4601056, 4603003, 4602959, 4603002, 4602958, 4601051, 4601054 |
| Microsoft Visual Studio | Important | Remote Code Execution | Find details on security updates for Visual Studio-related software in the Security Update Guide: https://msrc.microsoft.com/update-guide |
| Microsoft Dynamics-related software | Important | Information Disclosure | 4602915 |
| Microsoft Azure-related software | Important | Elevation of Privilege | Find details on security updates for Azure-related software in the Security Update Guide: https://msrc.microsoft.com/update-guide |
| Developer tools | Important | Remote Code Execution | Find details on security updates for developer tools in the Security Update Guide: https://msrc.microsoft.com/update-guide |
Notes:
- Find details for all updates in the monthly release in the Security Update Guide: https://msrc.microsoft.com/update-guide
- For additional details, see the release notes at: https://msrc.microsoft.com/update-guide/releaseNote/2021-Feb
Security vulnerability overview:
Below is a summary showing the number of vulnerabilities addressed in this release, broken down by product/component and by impact.
| Vulnerability Details | RCE | EOP | ID | SFB | DOS | SPF | TMP | Publicly Disclosed | Known Exploit | Max CVSS |
| Windows 10 v20H2 & Windows Server v20H2 | 10 | 7 | 5 | 2 | 4 | 0 | 0 | 3 | 1 | 9.8 |
| Windows 10 v2004 & Windows Server v2004 | 10 | 7 | 5 | 2 | 4 | 0 | 0 | 3 | 1 | 9.8 |
| Windows 10 v1909 & Windows Server v1909 | 10 | 6 | 5 | 2 | 3 | 0 | 0 | 3 | 1 | 9.8 |
| Windows 10 v1809 & Windows Server 2019 | 10 | 7 | 5 | 2 | 3 | 0 | 0 | 3 | 1 | 9.8 |
| Windows 10 v1803 | 7 | 6 | 4 | 2 | 3 | 0 | 0 | 3 | 1 | 9.8 |
| Windows Server 2016 | 10 | 5 | 3 | 1 | 2 | 0 | 0 | 1 | 0 | 9.8 |
| Windows 8.1 & Server 2012 R2 | 7 | 4 | 3 | 0 | 2 | 0 | 0 | 1 | 0 | 9.8 |
| Windows Server 2012 | 7 | 4 | 3 | 0 | 2 | 0 | 0 | 1 | 0 | 9.8 |
| Microsoft Office-related software | 4 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 7.8 |
| Microsoft SharePoint-related software | 2 | 0 | 1 | 0 | 0 | 1 | 0 | 0 | 0 | 8.8 |
| Lync/Skype for Business | 0 | 0 | 0 | 0 | 1 | 1 | 0 | 0 | 0 | 6.5 |
| Microsoft Exchange Server | 0 | 0 | 0 | 0 | 0 | 2 | 0 | 0 | 0 | 6.5 |
| Microsoft .NET-related software | 2 | 0 | 0 | 0 | 2 | 0 | 0 | 0 | 0 | 8.1 |
| Microsoft Visual Studio-related software | 2 | 0 | 0 | 0 | 1 | 0 | 0 | 1 | 0 | 7.8 |
| Microsoft Dynamics-related software | 0 | 0 | 1 | 0 | 0 | 1 | 0 | 0 | 0 | 6.5 |
| Microsoft Azure-related software | 0 | 2 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 7.0 |
| Developer tools | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 7.8 |
| RCE = Remote Code Execution | EOP = Elevation of Privilege | ID = Information Disclosure | SFB = Security Feature Bypass | DOS = Denial of Service | SPF = Spoofing | TMP = Tampering |
Resources for deploying updates to remote devices:
Part 1: Helping businesses rapidly set up to work securely from personal PCs and mobiles
Part 2: Helping IT send and provision business PCs at home to work securely during COVID-19
Part 3: Manage work devices at home during Covid-19 using Configuration Manager
Part 4: Managing remote machines with cloud management gateway (CMG)
Part 5: Managing Patch Tuesday with Configuration Manager in a remote work world
See also:
Mastering Configuration Manager Bandwidth limitations for VPN connected Clients
Vulnerability details for the current month:
Below are summaries for some of the security vulnerabilities in this release:
| Attack Vector | This metric reflects the context by which vulnerability exploitation is possible. The Base Score increases the more remote (logically, and physically) an attacker can be in order to exploit the vulnerable component. |
| Attack Complexity | This metric describes the conditions beyond the attacker’s control that must exist in order to exploit the vulnerability. Such conditions may require the collection of more information about the target or computational exceptions. The assessment of this metric excludes any requirements for user interaction in order to exploit the vulnerability. If a specific configuration is required for an attack to succeed, the Base metrics should be scored assuming the vulnerable component is in that configuration. |
| Privileges Required | This metric describes the level of privileges an attacker must possess before successfully exploiting the vulnerability. |
| User Interaction | This metric captures the requirement for a user, other than the attacker, to participate in the successful compromise the vulnerable component. This metric determines whether the vulnerability can be exploited solely at the will of the attacker, or whether a separate user (or user-initiated process) must participate in some manner. |
| CVE-2021-1727 | Windows Installer Elevation of Privilege Vulnerability |
| Impact | Elevation of Privilege |
| Severity | Important |
| Publicly Disclosed? | Yes |
| Known Exploits? | No |
| Exploitability | Exploitation more likely |
| CVSS Base Score | 7.8 |
| Attack Vector | Local |
| Attack Complexity | Low |
| Privileges Required | Low |
| User Interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
| Affected Software | All supported versions of Windows |
| More Information | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1727 |
| CVE-2021-1732 | Windows Win32k Elevation of Privilege Vulnerability |
| Impact | Elevation of Privilege |
| Severity | Important |
| Publicly Disclosed? | No |
| Known Exploits? | Yes |
| Exploitability | Exploitation detected |
| CVSS Base Score | 7.8 |
| Attack Vector | Local |
| Attack Complexity | Low |
| Privileges Required | Low |
| User Interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
| Affected Software | Windows 10 v20H2, Windows 10 v2004, Windows 10 v1909, Windows 10 v1809, Windows 10 v1803, Windows Server v20H2, Windows Server v2004, Windows Server v1909, and Windows Server 2019 |
| More Information | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1732 |
| CVE-2021-24074 | Windows TCP/IP Remote Code Execution Vulnerability |
| Impact | Remote Code Execution |
| Severity | Critical |
| Publicly Disclosed? | No |
| Known Exploits? | No |
| Exploitability | Exploitation more likely |
| CVSS Base Score | 9.8 |
| Attack Vector | Network |
| Attack Complexity | Low |
| Privileges Required | None |
| User Interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
| Affected Software | All supported versions of Windows |
| More Information | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-24074 |
| CVE-2021-24094 | Windows TCP/IP Remote Code Execution Vulnerability |
| Impact | Remote Code Execution |
| Severity | Critical |
| Publicly Disclosed? | No |
| Known Exploits? | No |
| Exploitability | Exploitation more likely |
| CVSS Base Score | 9.8 |
| Attack Vector | Network |
| Attack Complexity | Low |
| Privileges Required | None |
| User Interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
| Affected Software | All supported versions of Windows |
| More Information | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-24094 |
| CVE-2021- 24077 | Windows Fax Service Remote Code Execution Vulnerability |
| Impact | Remote Code Execution |
| Severity | Critical |
| Publicly Disclosed? | No |
| Known Exploits? | No |
| Exploitability | Exploitation less likely |
| CVSS Base Score | 9.8 |
| Attack Vector | Network |
| Attack Complexity | Low |
| Privileges Required | None |
| User Interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
| Affected Software | All supported versions of Windows |
| More Information | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-24077 |
| CVE-2021-24078 | Windows DNS Server Remote Code Execution Vulnerability |
| Impact | Remote Code Execution |
| Severity | Critical |
| Publicly Disclosed? | No |
| Known Exploits? | No |
| Exploitability | Exploitation more likely |
| CVSS Base Score | 9.8 |
| Attack Vector | Network |
| Attack Complexity | Low |
| Privileges Required | None |
| User Interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
| Affected Software | Windows Server v20H2, Windows Server v2004, Windows Server v1909, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, and Windows Server 2012 |
| More Information | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-24078 |
| CVE-2021-24088 | Windows Local Spooler Remote Code Execution Vulnerability |
| Impact | Remote Code Execution |
| Severity | Critical |
| Publicly Disclosed? | No |
| Known Exploits? | No |
| Exploitability | Exploitation less likely |
| CVSS Base Score | 8.8 |
| Attack Vector | Network |
| Attack Complexity | Low |
| Privileges Required | Low |
| User Interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
| Affected Software | All supported versions of Windows |
| More Information | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-24088 |
| CVE-2021-24098 | Windows Console Driver Denial of Service Vulnerability |
| Impact | Denial of Service |
| Severity | Important |
| Publicly Disclosed? | Yes |
| Known Exploits? | No |
| Exploitability | Exploitation less likely |
| CVSS Base Score | 5.5 |
| Attack Vector | Local |
| Attack Complexity | Low |
| Privileges Required | None |
| User Interaction | Required |
| Scope | Unchanged |
| Confidentiality | None |
| Integrity | None |
| Availability | High |
| Affected Software | Windows 10 v20H2, Windows 10 v2004, Windows 10 v1909, Windows 10 v1809, Windows 10 v1803, Windows Server v20H2, Windows Server v2004, Windows Server v1909, and Windows Server 2019 |
| More Information | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-24098 |
| CVE-2021-24066 | Microsoft SharePoint Remote Code Execution Vulnerability |
| Impact | Remote Code Execution |
| Severity | Important |
| Publicly Disclosed? | No |
| Known Exploits? | No |
| Exploitability | Exploitation more likely |
| CVSS Base Score | 8.8 |
| Attack Vector | Network |
| Attack Complexity | Low |
| Privileges Required | Low |
| User Interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
| Affected Software | Microsoft SharePoint Server 2019, Microsoft SharePoint Enterprise Server 2016, Microsoft SharePoint Foundation 2013 Service Pack 1, and Microsoft SharePoint Foundation 2010 Service Pack 2 |
| More Information | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-24066 |
| CVE-2021-24067 | Microsoft Excel Remote Code Execution Vulnerability |
| Impact | Remote Code Execution |
| Severity | Important |
| Publicly Disclosed? | No |
| Known Exploits? | No |
| Exploitability | Exploitation less likely |
| CVSS Base Score | 7.8 |
| Attack Vector | Local |
| Attack Complexity | Low |
| Privileges Required | None |
| User Interaction | Required |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
| Affected Software | Microsoft 365 Apps for Enterprise, Excel 2016, Excel 2013, Excel 2010, Office Online Server, Office 2019, Office 2019 for Mac, and Office Web Apps Server 2013 |
| More Information | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-24067 |
February 2021 Microsoft Office security updates
Microsoft Office security updates are delivered through the Microsoft Update platform and via the Download Center.
Patched Office security vulnerabilities – (Source: Bleeping Computer)
This month’s Office security updates address bugs exposing Windows systems running vulnerable Click to Run and Microsoft Installer (.msi) based editions of Microsoft Office products to remote code execution (RCE), information disclosure, and spoofing attacks.
Microsoft rated the six RCE bugs patched in February 2021 as Important severity issues given that they could enable attackers to execute arbitrary code in the context of the currently logged-in user.
Following successful exploitation, attackers could install malicious programs, view, change, and delete data, as well as make their own admin accounts on exploited Windows devices.
| Tag | CVE ID | CVE Title | Severity |
| Microsoft Office Excel | CVE-2021-24067 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2021-24068 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2021-24069 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2021-24070 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-24071 | Microsoft SharePoint Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-1726 | Microsoft SharePoint Spoofing Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-24066 | Microsoft SharePoint Remote Code Execution Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-24072 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Important |
Further information about each of them is available within the knowledge base articles linked below.
Microsoft Office 2016:
| Product | Knowledge Base article title and number |
|---|---|
| Excel 2016 | Description of the security update for Excel 2016: February 9, 2021 (KB4493196) |
| Office 2016 | February 2, 2021, update for Office 2016 (KB4493189) |
| Outlook 2016 | February 2, 2021, update for Outlook 2016 (KB4493190) |
| PowerPoint 2016 | February 2, 2021, update for PowerPoint 2016 (KB4493164) |
Microsoft Office 2013:
| Product | Knowledge Base article title and number |
|---|---|
| Excel 2013 | Description of the security update for Excel 2013: February 9, 2021 (KB4493211) |
| Office 2013 | February 2, 2021, update for Office 2013 (KB4486684) |
| PowerPoint 2013 | February 2, 2021, update for PowerPoint 2013 (KB4493169) |
Microsoft Office 2010:
| Product | Knowledge Base article title and number |
|---|---|
| Excel 2010 | Description of the security update for Excel 2010: February 9, 2021 (KB4493222) |
| Office 2010 | February 2, 2021, update for Office 2010 (KB4493180) |
| PowerPoint 2010 | February 2, 2021, update for PowerPoint 2010 (KB4493179) |
Microsoft SharePoint Server 2019:
| Product | Knowledge Base article title and number |
|---|---|
| Office Online Server | Description of the security update for Office Online Server: February 9, 2021 (KB4493192) |
| SharePoint Server 2019 | Description of the security update for SharePoint Server 2019: February 9, 2021 (KB4493194) |
| SharePoint Server 2019 Language Pack | February 9, 2021, update for SharePoint Server 2019 Language Pack (KB4493193) |
Microsoft SharePoint Server 2016:
| Product | Knowledge Base article title and number |
|---|---|
| SharePoint Enterprise Server 2016 | Description of the security update for SharePoint Enterprise Server 2016: February 9, 2021 (KB4493195) |
Microsoft SharePoint Server 2013:
| Product | Knowledge Base article title and number |
|---|---|
| Office Web Apps Server 2013 | Description of the security update for Office Web Apps Server 2013: February 9, 2021 (KB4493204) |
| Project Server 2013 | February 9, 2021, cumulative update for Project Server 2013 (KB4493207) |
| SharePoint Enterprise Server 2013 | February 9, 2021, cumulative update for SharePoint Enterprise Server 2013 (KB4493209) |
| SharePoint Foundation 2013 | Description of the security update for SharePoint Foundation 2013: February 9, 2021 (KB4493210) |
| SharePoint Foundation 2013 | February 9, 2021, cumulative update for SharePoint Foundation 2013 (KB4493205) |
Microsoft SharePoint Server 2010:
| Product | Knowledge Base article title and number |
|---|---|
| Project Server 2010 | February 9, 2021, update for Project Server 2010 (KB4475537) |
| Project Server 2010 | February 9, 2021, cumulative update for Project Server 2010 (KB4493217) |
| SharePoint Foundation 2010 | Description of the security update for SharePoint Foundation 2010: February 9, 2021 (KB4493223) |
| SharePoint Server 2010 | February 9, 2021, cumulative update for SharePoint Server 2010 (KB4493220) |
| SharePoint Server 2010 | February 9, 2021, update for SharePoint Server 2010 (KB4493212) |
| SharePoint Server 2010 Office Web Apps | February 9, 2021, update for SharePoint Server 2010 Office Web Apps (KB4493219) |