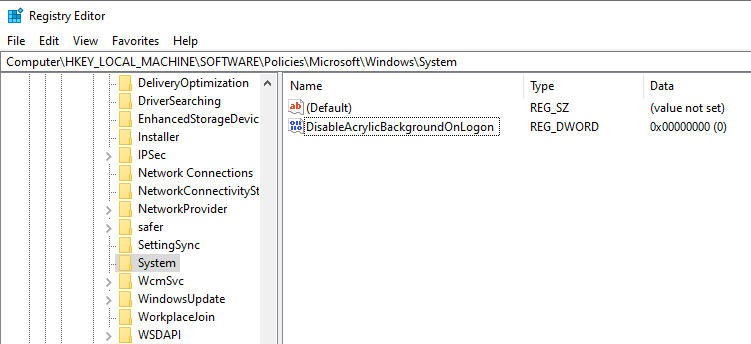
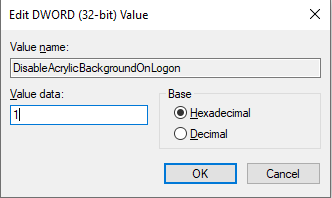
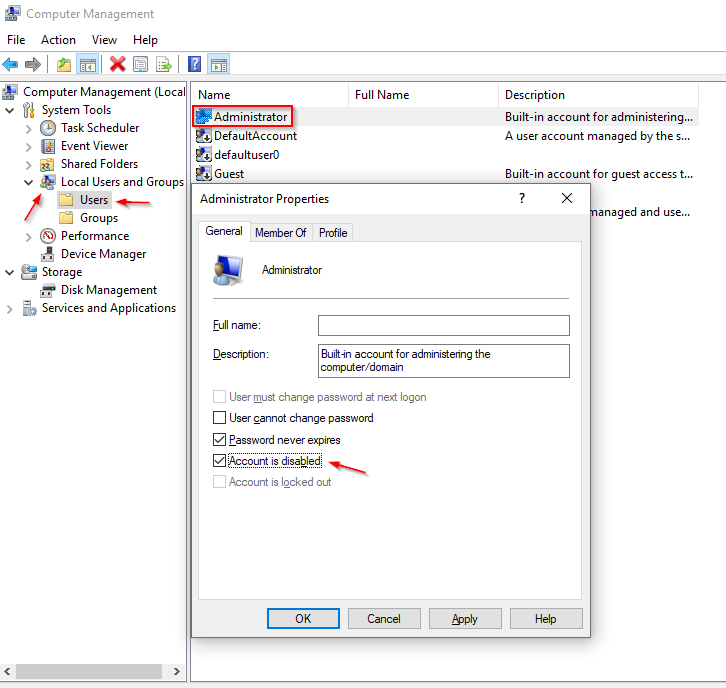
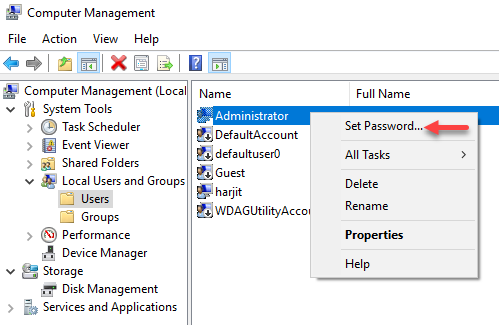
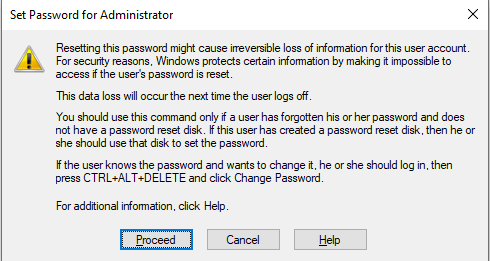
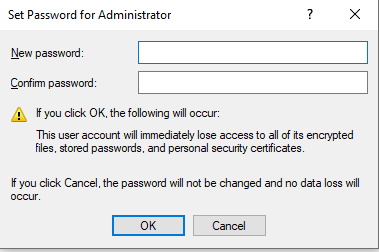
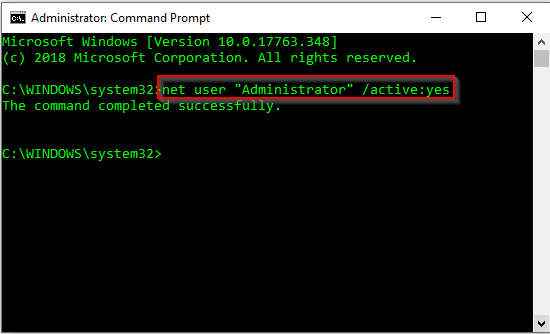
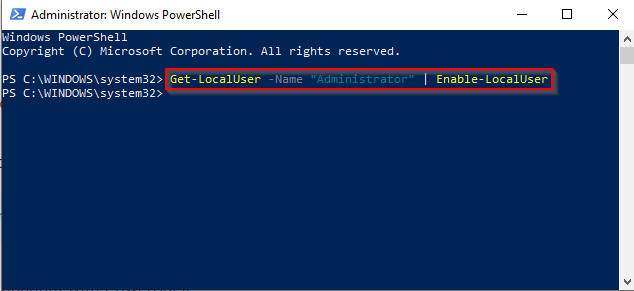
So, you’re headed to the Midwest Management Summit aka MMSMOA in Minneapolis, Minnesota from May 14-17, 2018 and with just a few days to go, now comes the dilemma of what to pack. Here are some suggestions from a conference veteran like me to help you with the task of packing.
What to Pack:
#1: Shoes – Comfortable shoes to wear during the conference is always a good thing to have. The nice thing about MMSMOA is that everything from sessions to expo hall is located in one general area which is in the Raddison Blu Hotel at The Mall of America. You have a very short walk from your hotel room, down the elevator and then just a few feet to get to all the session rooms. Most of your walking time will involve getting lunch or dinner, and to do some shopping at the massive Mall of America.
#2: Tech – Start collecting all the cables and charges you’ll need to keep your devices up and running at the conference. I recommend that you pack a portable battery charger for your smartphone(s), especially helpful when you are on-the-go and the power outlets are not easily accessible. It’s also advisable to pack a small power strip as power outlets can be scarce and you’ll make friends by sharing an outlet with others. This is also handy to use in your hotel room where the power outlets could be inaccessible due to their location (behind the bed, behind the entertainment system, etc). As for the portable battery chargers, I’m a big fan of the Anker brand for their ruggedness, quality, capacity, and great customer service when I need them.
#3: Clothes – The setting for the conference including the social events is casual. Pack comfortable clothes, but don’t pack too much since the conference is 4 days long. A few vendors will hand out free t-shirts, plus if you’re in a bind, the mall is conveniently located where you can quickly shop for something that you may need. You’ll definitely want to pack the essential items such as socks, underwear, a hoodie or sweatshirt for the cold conference rooms, a pair of jeans or casual pants, a few shirts, and whatever else you think is essential. Don’t forget your toiletries too.
** If you’re a dude, please for God sake leave the “manpris” at home! **
#4: Bottle / Mug – A traveling coffee mug if you’re a coffee drinker. Makes it easier to fill up on coffee and to travel from session to session without spilling. Plus, you’re helping safe the planet without using the disposable cups. You could also bring a water bottle as you should re-hydrate often.
#5: Cards – Bring along some business cards for networking purposes as well as to enter some cool contests organized by several vendors. I generally get my cards ordered in advance from Moo as I prefer the mini-card format and the high quality. You can also order some inexpensive business cards from VistaPrint but since it’s late in the game now to get some cards ordered in time for the conference, either make some at home with your personal printer or order some in-store at places like Staples.
#6: Social Media – Networking is one of the most important aspects of attending a conference such as MMSMOA. By now you have connected with several attendees and speakers via Twitter, Facebook, LinkedIn, WhatsApp, and/or Slack. If you haven’t, then it’s time you get on the social media band wagon to collaborate with others, make some new friends, help to enhance your career, don’t feel left out at the conference, and etc. One tip for helping with the process on location and to make the social media connections as smooth as possible is to print QR Codes of your favorite social media medium such as Twitter or Facebook. This way, you can easily whip out your QR Code when you meet someone that you’d like to connect and they can easily scan the code with their smartphone which will pull up your information with ease. Keep in mind, Twitter is preferred and encouraged to use at MMSMOA. Don’t forget to follow @MMSMOA on Twitter and use the hashtag #MMSMOA for all your tweets! You can follow me as well: @Hoorge.
#7: Luggage – You should be good with your main suitcase or bag that you will pack with your clothes and the above items. Abundance of swag is not something you will collect at this conference, other than a few small trinkets and a couple of t-shirts. If you are planning to do some crazy shopping at the Mall of America, then an extra bag will come in handy.
#8: Laptop / Tablet – I generally travel with two laptops, one in case I need to jump in to handle some work issues back at the office, and the other as a personal device for daily use. Another reason for traveling with more than one laptop is in case one of them crashes for whatever reason and I still have something to manage my personal and work life. As far as note taking goes at the conference, I tend to use my iPhone as my primary device along with OneNote and Twitter apps. If you have been my follower on Twitter, you’ll know how much I use that medium for note taking, as I do that quite efficiently with unique hashtags for each session and other matters related to the conference. So, if you’re not following me, do so now. You’ll find me as @Hoorge on Twitter.
#9: Medical – If you take any prescription medication, make sure you bring those and preferably in their original packaging, and this is to avoid any issues with TSA at the airport. I travel with my CPAP machine for my sleep apnea, so I always make sure that I have the power cord, hose, mask, and other fun stuff that goes with the machine packed as a priority item the morning that I’m leaving for the airport. If you use spectacles and have an extra pair, bring that with you incase you encounter an unfortunate accident and break your main “four eyes”.
#10: Smartphone – I think it goes without saying that you won’t be traveling to the conference without your smartphone. To make your life a little easier, make sure you have enough free space to capture photos and videos during the week. Also, if you haven’t already done so, install apps such as OneNote for note taking; Twitter and Facebook for social media; OneDrive or Dropbox for uploading photos and videos to free up space on your device and for backup purposes; Microsoft Office Lens for capturing whiteboards, slide decks, business cards, and more; WhatsApp, Messenger and Slack for communication; and last but not least Untappd if you’re a beer lover.
#11: Camera – There are always some wonderful opportunities for capturing some great photos of the conference, so bring a camera with you. I would avoid bringing a large professional DSLR type camera with lenses and speedlights such as the Nikon D700 camera and the 24-70mm f/2.8 lens I often use for my freelance photojournalism work and event photography as it’ll be cumbersome to travel with and juggle during the conference. I tend to rely on my nifty iPhone for all of my photography and videography captures, and sometimes I bring along my Samsung NX300 camera for good measure. I’ll leave the selfie stick at your discretion.
#12: Fitness Trackers – No doubt there’s going to be some amount of walking during MMSMOA between the hotel and the mall, so don’t forget to pack your fitness tracker units like Fitbit, smart watches and their respective charging units to see if you break any step records. Find a few friends and do a step challenge for the week.
#13: Credit Cards / Cash – At this conference, you are on your own for breakfast, lunch, and dinner, so plan your finances accordingly. I would carry a small amount of cash for incidentals and tips or when you need to split a bill with others. Credit Cards is the way to go for everything else but beware and pay attention to your statements as fraudulent charges have been reported by attendees from past conferences such as Microsoft Ignite, sometimes even 6 months after the fact. If you want some peace of mind and avoid the hassle of compromised credit cards, get a couple of prepaid credit cards with limited amounts on them to use in restaurants, bars, and other establishments.
#14: Snacks – Each day at the conference can be long, tough, and super busy as you move from session to session and network with fellow attendees. Sometimes, it can be a challenge to spare some time for breakfast or lunch, so food items such as granola bars, health bars, nuts, and pop tarts can be extremely helpful. There is a Cariboo Coffee store just steps away from all the action in case you need to pickup some food and drinks.
#15: Sriracha and Beer – It goes without saying, I travel with my favorite hot sauce to spice up my conference center meals. How so you ask? Well, I often travel with the Sriracha2Go keychain container or the Sriracha2Go packets and they are so handy to have if you like to spice up your food on the go. As for beer, it’s a great way to network and try out some craft beer from all over the country and even abroad. Pack some of your local craft beer in your suitcase and enjoy them with some old and new friends. Don’t forget to double ziplock bag them and wrap them with your clothing to avoid breakage.
#16: Trinkets / Souvenirs – It’s never a bad idea to bring a few little trinkets from your local town / city / state / country such as keychains, stickers, fridge magnets, candy, etc to hand out or exchange with a fellow attendees. They become conversational items and everyone loves a little gift.
Hope this list will help you to pack for the conference and is helpful for things you may not have thought about. Good luck and see you soon in Minneapolis!
Follow (@Hoorge) on Twitter and join Tech Konnect on Facebook and Twitter (@TechKonnect) to stay current on technology related matters.